问题描述
我想在答案中回答的一些问题:
-
我如何知道 apparmor 是否正在运行?
-
我怎么知道它是否运作良好?
最佳方案
要了解 app-armor 的状态,请在终端中键入此命令。
sudo apparmor_status
例如,示例输出:
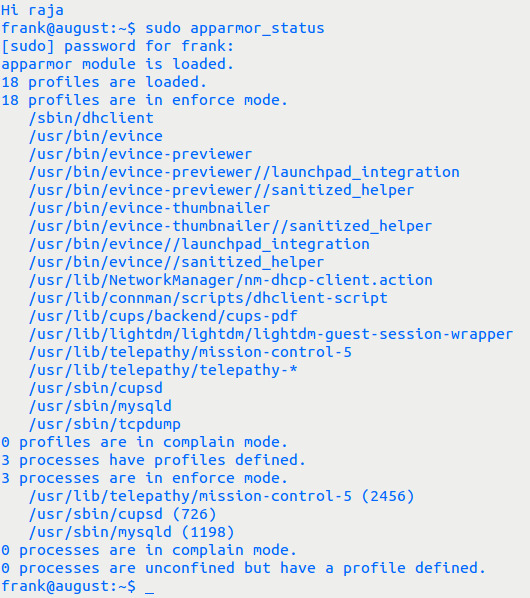
为了提供 Apparmor 的工作性能,我认为没有测量工具。据我所知,我们必须通过您的 PC 周围发生的事情来检测它,我的意思是异常。
次佳方案
要解决这个子问题:我如何判断它是否运行良好?
Apparmor 配置文件正在进行中。因此,球门柱正在移动。请查看 \n Poking Holes in AppArmor Profiles 和 Canonical 的 Jamie Strandboge here 的回复。我希望这两个链接能让您了解问题的复杂性。
您是否希望保留子问题作为问题的一部分由您决定。
提前为此 “non-answer” 致歉。
编辑以进一步说明为什么这个子问题至少可以说取决于上下文:
考虑最流行的程序之一:Firefox。它有一个配置文件,但它以抱怨模式而不是强制模式发送。换句话说,Apparmor 对开箱即用的 Firefox 没有任何作用。原因在 here 中陈述,尽管很简短:
\\n
The end-user impact for users in default installations will be non-existent. The firefox package will ship in complain-mode during the development cycle and before release (or at some point in the cycle) be updated to be disabled. Users must opt-in to using the profile and therefore should know that AppArmor confinement could cause firefox to behave unexpectedly.
\\n
接下来,考虑当仅 “heard” 或 “read” 关于 Apparmor 的普通用户将配置文件置于强制模式时会发生什么。毫无疑问,有一种成就感。
然后,看看 2010 年的 this bug,忽略粗鲁的部分。注意标题:“firefox apparmor profile is too lenient”。继续阅读评论 #4 中的部分理由:
\\n
AppArmor can protect against many things. The firefox profile protects against execution of arbitrary code by the browser and reading/writing of files you do not own (eg /etc/passwd), reading/writing sensitive files like the user’s gnome-keyring, ssh keys, gnupg keys, history files, swp, backup files, rc files and to files in the standard PATH. It also confines add-ons and extensions to the above. Firefox is integrated into the Desktop and so it must be allowed to open helper programs and access the user’s data. The profile is by default general purpose with the design being:
\\n * when enabled, it significantly improves the security of firefox as is
\\n * it provides a starting point for people to confine firefox how they want to
\\n * the implementation gives the user the ability to fine-tune it to be as strict as desired
\\n Of course firefox can be locked down more to protect the user’s data. We could make it so that it could only write to ~/Downloads and read from ~/Public. However, this deviates from upstream’s design, would likely put Ubuntu’s Mozilla branding at stake, and most importantly frustrate users. Is Ubuntu’s profile a “violation of the idea of apparmor”? Of course not — it is protecting user’s from various attacks and many forms of information disclosure. It is a distribution requirement to provide a functional browser. It is a distribution choice to not break it with too-aggressive security protections. It is a user’s/administrator’s choice to configure the profile for her environment.\\n
类似的论点适用于 Evince。
